Fake Bun runtime infects over 1,000 NPM packages and 27,000 Github repositories with malware in just a few hours

On November 24, 2025, local time,
Shai-Hulud Returns: Over 1K NPM Packages and 27K+ Github Repos infected via Fake Bun Runtime Within Hours — HelixGuard
https://helixguard.ai/blog/malicious-sha1hulud-2025-11-24
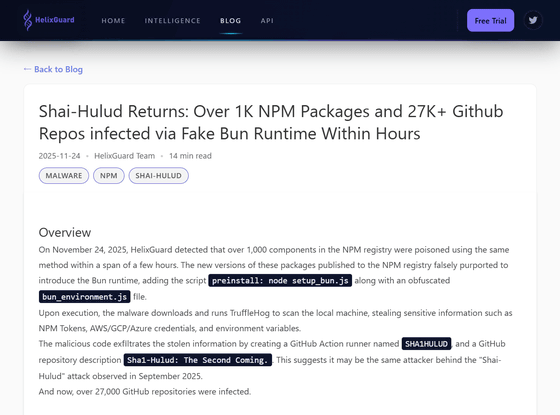
According to HelixGuard, over 1,000 components in the NPM registry were compromised using the same technique in just a few hours. The compromised components in the NPM registry falsely claim to 'introduce the Bun runtime' and have been confirmed to contain scripts and an obfuscated file (bun_environment.js).
The scripts added are as follows:
[code]preinstall: node setup_bun.js[/code]
The obfuscated file, 'bun_environment.js,' is a malicious JavaScript file that is over 10MB in size and contains a huge amount of logic for stealing information.
When this obfuscated file is executed, the malware downloads and executes TruffleHog , a tool that automatically checks for committed credentials from Git repositories, to steal sensitive information from the local machine, including npm tokens, AWS, Google Cloud, and Azure credentials, and environment variables.
The malicious script also modifies 'package.json' based on the npm configuration in the current environment to inject 'setup_bun.js' and 'bun_environment.js', then repackages the components and runs 'npm publish' with the stolen token, spreading like a worm.
To send the stolen confidential information, the malicious script creates a workflow file named '.github/workflows/formatter_123456789.yml' and creates a GitHub Actions runner named 'SHA1HULUD.' This workflow processes repository secrets using double Base64 encoding and saves them together in a file called 'actionsSecrets.json.'
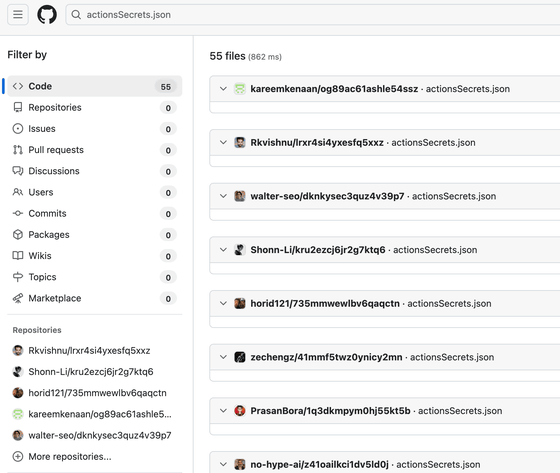
Then, a GitHub repository with the description 'Sha1-Hulud: The Second Coming' is generated. At the time of writing, there are more than 27,000 GitHub repositories with this name.
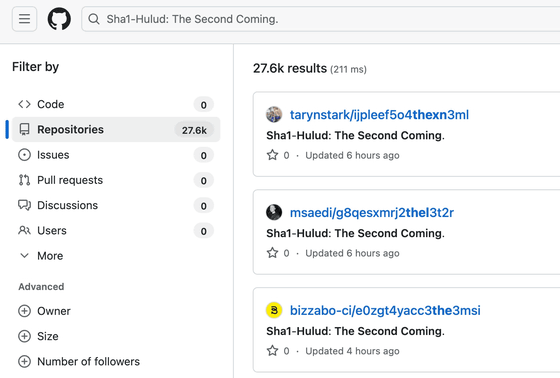
Based on this name, it has been pointed out that the perpetrator of this cyber attack may be the same person who carried out the supply chain attack 'Shai-Hulud.'
The popular @ctrl/tinycolor package, downloaded over 2 million times per week, has been compromised along with over 40 other NPM packages by a sophisticated supply chain attack called 'Shai-Hulud' - GIGAZINE

Related Posts:
in Security, Posted by logu_ii