How have ordinary citizens resisted the Chinese government's internet censorship, the 'Great Firewall'?

China has a massive internet censorship system known as the '
A Brief, Incomplete, and Mostly Subjective History of Chinese Internet censorship and its countermeasures
https://danglingpointer.fun/posts/GFWHistory
Ma says that for almost as long as he has been using the internet in China, ordinary citizens seeking freedom have been fighting against China's Great Firewall. However, he said that he was unable to find a complete record of the technological battles and developments between the two, as well as their complex history, so he decided to write about his own experiences. Ma also said that his account relies solely on his subjective memories, and that some of the dates and details of events may be inaccurate.
The dawn of the Internet in China
China's first foray into the internet world was in 1987, when an email was sent to Germany that read, 'Once you cross the Great Wall, you can reach every corner of the world.' This email was a kind of prophecy, Ma said.
For the next 12 years or so, there were no technical restrictions on internet use in China. For a long time, internet access in China was limited to a minority due to the high cost and complexity of computers.

The early Great Firewall and VPNs
In 1998 (or, according to some sources, 2002), China introduced
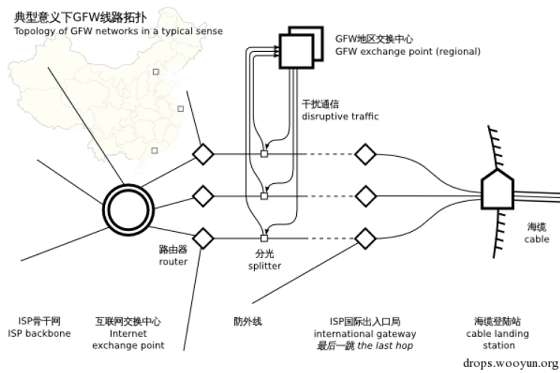
Realizing that DNS spoofing alone was not enough, the censors deployed special hardware devices at backbone network nodes, such as prefectural border routers and submarine cable landing stations . These devices intercept network traffic through beam splitters and, if a connection is established with a blacklisted IP address, send a RST packet to reset the connection.
Below is a diagram illustrating the censorship technique, which involved attaching special devices to network nodes. These devices are said to have formed the initial hardware basis of the Great Firewall.
In addition to IP address blacklists, the Great Firewall also implemented keyword-based filters that would reset connections if they detected sensitive content, such as the names of government officials or scandals. Ma explains that this was possible because
At the time, the Great Firewall was focused on blocking direct access to 'inappropriate content' and didn't allow for user-side circumvention. Therefore, it was relatively easy for users to circumvent the Great Firewall using proxies or VPNs based on standard protocols. Ma's experience shows that these simple solutions were still working to a limited extent as of 2014.
◆Early 2010s
However, in the 2010s, censors also began to take action against VPNs, actively blacklisting VPN IP addresses. Users had to create a long list of VPNs, ensuring that at least one was not blacklisted. Meanwhile, VPN Gate , a VPN relay server project led by the University of Tsukuba, became a good option for users seeking freedom in China.
Also popular were VPNs such as FreeGate and Wujie, operated by political organizations hostile to the Chinese government. These groups were highly motivated and well-funded, Ma said, making them trustworthy. The downside, Ma said, was that when users launched these VPN services, they would always redirect their browsers to political propaganda websites.
◆GoAgent
Savvy tech users eventually popularized the 'private foreign node' solution, based on the idea that establishing a private proxy server and keeping it secret would prevent censors from detecting it. A popular hosting service was GoAgent , which allowed anyone to create their own Google App Engine instance and obtain a personal proxy node. Unfortunately, GoAgent was shut down in late 2014 under pressure from the Chinese government.

The End of VPNs and Shadowsocks
The Great Firewall was later upgraded to detect and block the use of VPN services by detecting the unique traffic that VPNs use. This censorship method was so powerful that it rendered a wide variety of protocols unusable.
One of the few services that survived this upgrade was Shadowsocks , which uses a pre-defined key algorithm to enable encrypted communications using Socks 5 , making it extremely difficult to identify traffic patterns. Ma points out that Shadowsocks is the first protocol family to actively consider adversaries like the Great Firewall.
The Great Firewall tried to detect Shadowsocks by focusing on the length of TCP packets , which remains unchanged even with Shadowsocks encryption. Furthermore, later versions of Shadowsocks added random packets to messages sent by the censors, allowing them to proactively identify Shadowsocks proxies.
Chinese users have used various obfuscation techniques on Shadowsocks, even mimicking common protocols like HTTP, Skype, and WeChat. The original Shadowsocks repository was once removed due to government pressure, but people have continued to create forks of it and use them to circumvent censorship. 'Over the past decade, Shadowsocks has been extremely influential in the Chinese proxy community,' Ma said.

The emergence of V2Ray and HTTPS
V2Ray , which appeared in 2016, was a game changer for users wanting to bypass the Great Firewall. V2Ray was equipped with a flexible and detailed JSON-based proxy architecture control system, allowing users to configure everything from the inbound protocols entering the system, to the routing rules to be filtered, to the outbound protocols to be ultimately sent. This extensibility was remarkable compared to previous proxy configuration systems.
Since then, V2Ray and its successor frameworks have diversified the proxy ecosystem, improving the user experience and lowering the barrier to entry for new users. The vast number of proxy combinations was a major challenge for the Great Firewall, but the outbound/inbound protocols themselves were weak points, and if the Great Firewall could identify all protocols, they would be blocked.
That's where HTTPS came in. It allowed structured content to be transformed into bytes that were statistically indistinguishable from randomly played content. By proxying any traffic and encrypting it with HTTPS, censors could no longer determine its content simply by looking at the bytes. Furthermore, methods were devised to reduce the computing costs associated with HTTPS encryption, so CPU performance was no longer a bottleneck for proxies.
However, HTTPS encryption doesn't solve all problems. Many users connect to a single proxy server for extended periods of time, which appears to censors as 'visiting niche HTTPS sites for hours on end.' By detecting this suspicious activity, it's possible to identify users circumventing censorship.
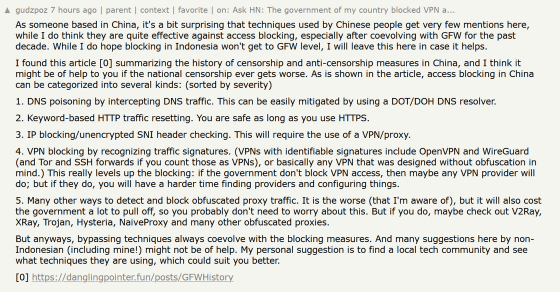
Ma's blog was mentioned on the social news site Hacker News in connection with the topic of VPNs being blocked in Indonesia . The Hacker News user commented, 'As a resident of China, I'm a little surprised that the tactics used by Chinese people are barely mentioned here,' and suggested that China's experience may be useful to Indonesians.
As someone based in China, it's a bit surprising that techniques used by Chinese... | Hacker News
https://news.ycombinator.com/item?id=45056420
Related Posts:
in Note, Software, Web Service, Security, Posted by log1h_ik