Suspicion emerges that Elon Musk's software engineers were involved in the 'extraction of classified information from government organizations by the Department of Government Efficiency (DOGE)'

by
It has been reported that a DOGE employee with a background as a software engineer at X (formerly Twitter) and SpaceX may have been involved in the alleged theft of several gigabytes of data from classified case files at the National Labor Relations Board (NLRB), an independent administrative agency of the US government that enforces labor laws.
DOGE Worker's Code Supports NLRB Whistleblower – Krebs on Security
https://krebsonsecurity.com/2025/04/doge-workers-code-supports-nlrb-whistleblower/
Daniel Berles, a whistleblower who works in the NLRB's IT department, alleged that DOGE officials came to the NLRB to access its internal systems and exfiltrated large amounts of data, including potentially confidential information about labor unions, ongoing litigation and trade secrets.
A whistleblower revealed details of how DOGE, led by Elon Musk, accessed the National Labor Relations Board's internal system and extracted confidential information, disabling monitoring tools and deleting traces, causing a sudden increase in access from Russian IP addresses - GIGAZINE

DOGE officials requested a senior-level account to access the NLRB's internal systems. When Berles subsequently investigated the systems, he found that most of the records related to network resources were missing and that monitoring tools had been disabled.
Additionally, Berles discovered an account that appears to have been created for DOGE: 'DogeSA_2d5c3e0446f9@nlrb.microsoft.com.' PowerShell command execution logs showed that this account was downloading three repositories from GitHub.
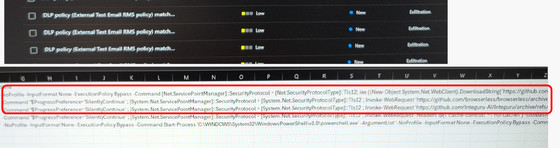
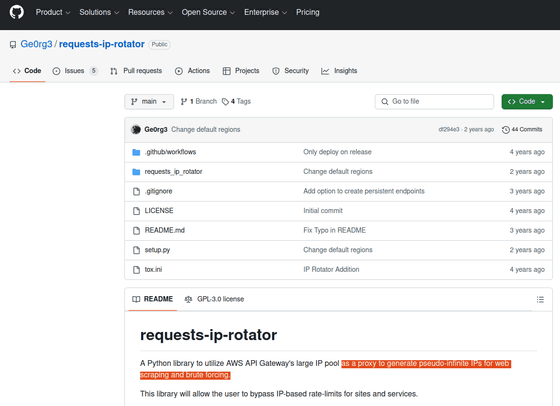
The README for one of these three programs states, 'Uses AWS API Gateway to generate pseudo-infinite IP addresses for web scraping and brute force attacks.' A Google search for this description leads to a program called '
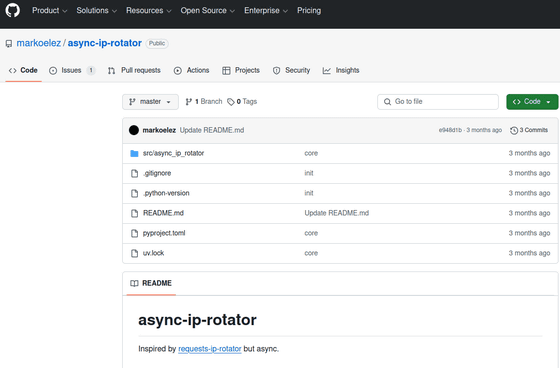
Furthermore, security researcher Brian Krebs' investigation revealed that DOGE employee Marco Erez had committed a fork of requests-ip-rotator called async-ip-rotator in January 2025.
Erez is a 25-year-old software engineer who has worked on several companies run by Elon Musk, including software development for SpaceX and search AI development for X (formerly Twitter). At DOGE, he is known for requesting administrator-level access to the U.S. Treasury Department's payment system, and was subject to severe public criticism for posting racist comments online. Erez once resigned from DOGE, but was rehired after President Donald Trump and Vice President J.D. Vance expressed their support.
Concerns raised over DOGE's access to government systems, 'potentially the most significant security breach in the history of the US government' - GIGAZINE

Krebs speculates that Erez may have been involved in the theft of confidential data from the NLRB, given that requests-ip-rotator is a tool that makes it difficult to track people on the Internet, and that Erez, who committed a fork of it, had access to internal systems at other government organizations as part of DOGE.
Shortly after Krebs published his article, Erez's async-ip-rotator repository was deleted and is no longer available. Before it was deleted, the async-ip-rotator issue had a comment criticizing the code's maturity, saying it was 'insecure, unscalable and a fundamental engineering failure.'
Related Posts: