Google pays 1.64 million yen in reward money for bug that extracts email addresses from YouTube accounts
Security researcher Skull has disclosed a vulnerability that allows him to obtain the email addresses of all YouTube users in a blog post. Skull reported this issue to Google and received a $10,633 reward.
Leaking the email of any YouTube user for $10,000
https://brutecat.com/articles/leaking-youtube-emails
Leaking the email address of every YouTube user ($10k bounty) - YouTube
In the comments section of YouTube live streams, there is a menu that allows you to report or block each comment.
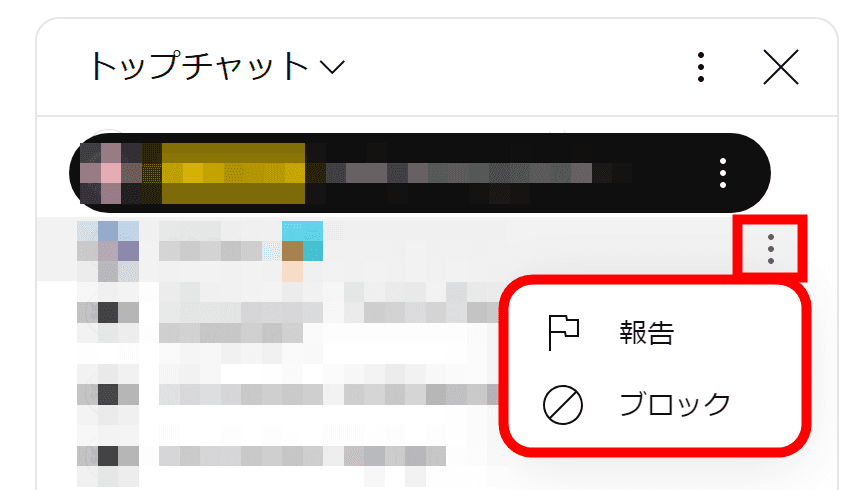
When you open the menu, the API will retrieve information to allow you to report or block the person.
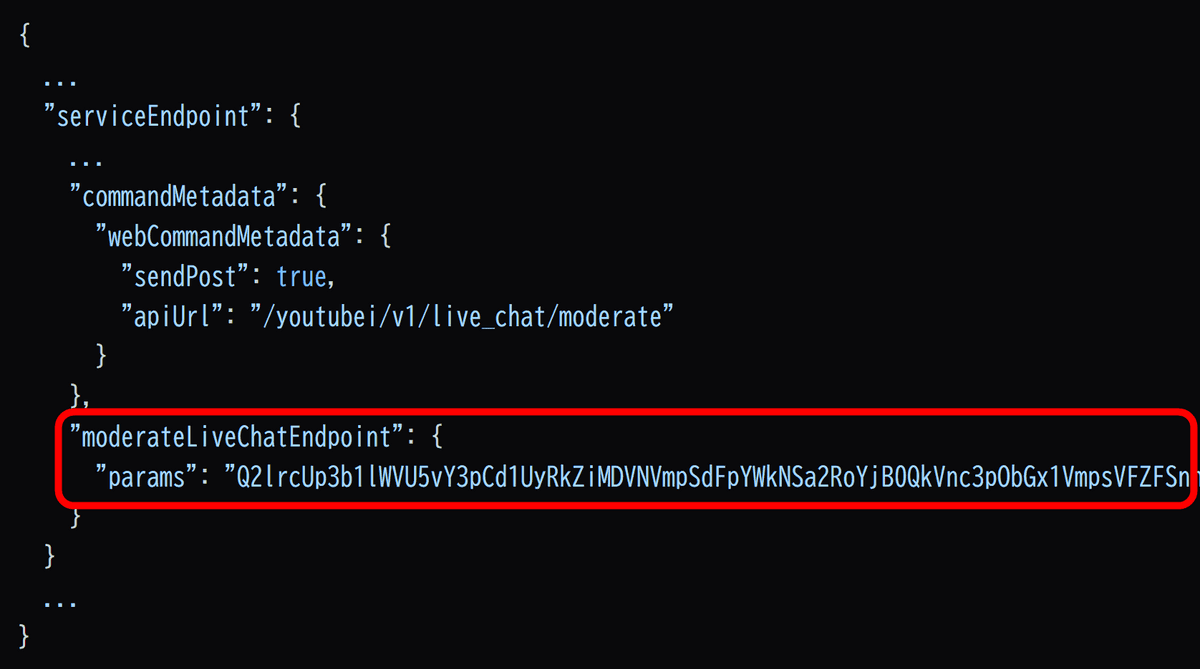
This information includes the 'Gaia ID,' which is essentially the ID for a Google account. Even if the Gaia ID is linked one-to-one with a Google account internally, there would have been no problem if there was no way to link the Gaia ID to a Google account.
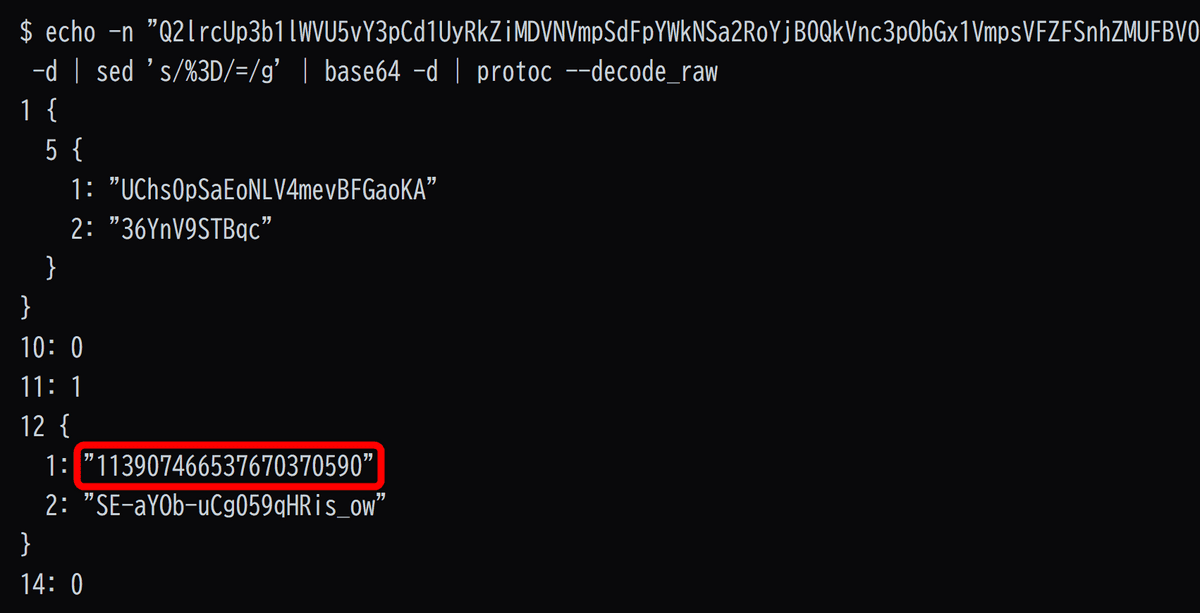
Skull and his friends worked together to investigate past Google services to find out how to link Gaia ID to a Google account. As a result, they discovered a problem with the sharing function of the Google Pixel's recorder app.
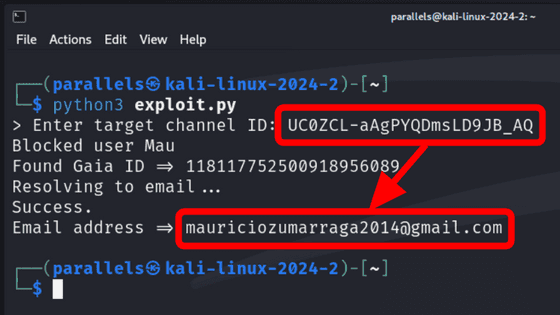
When you make a request to the recording sharing API using your Gaia ID, the email address of your Google account is returned.
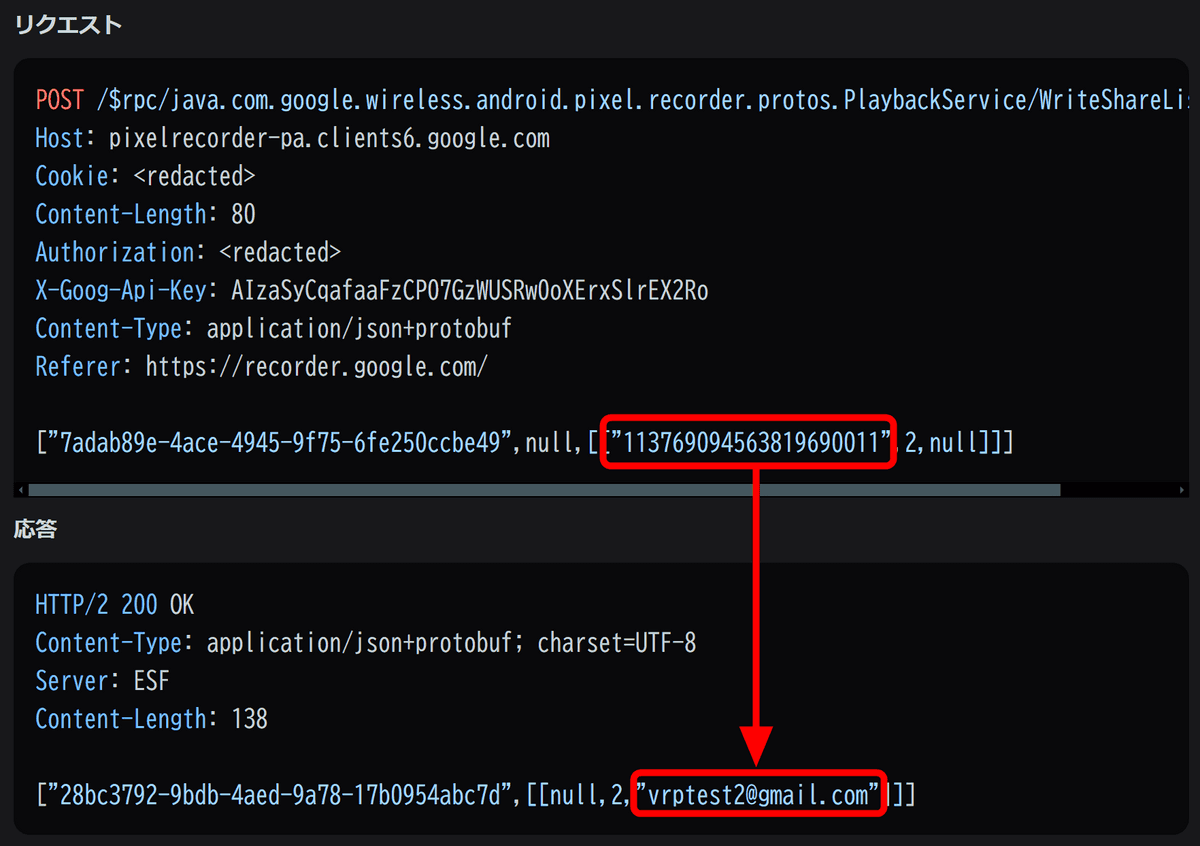
Luckily, since this is a sharing API, if you use it to link your Gaia ID to your Google account, you will receive an email notifying you that a recording has been shared, so the account owner may be aware that something fishy is going on.
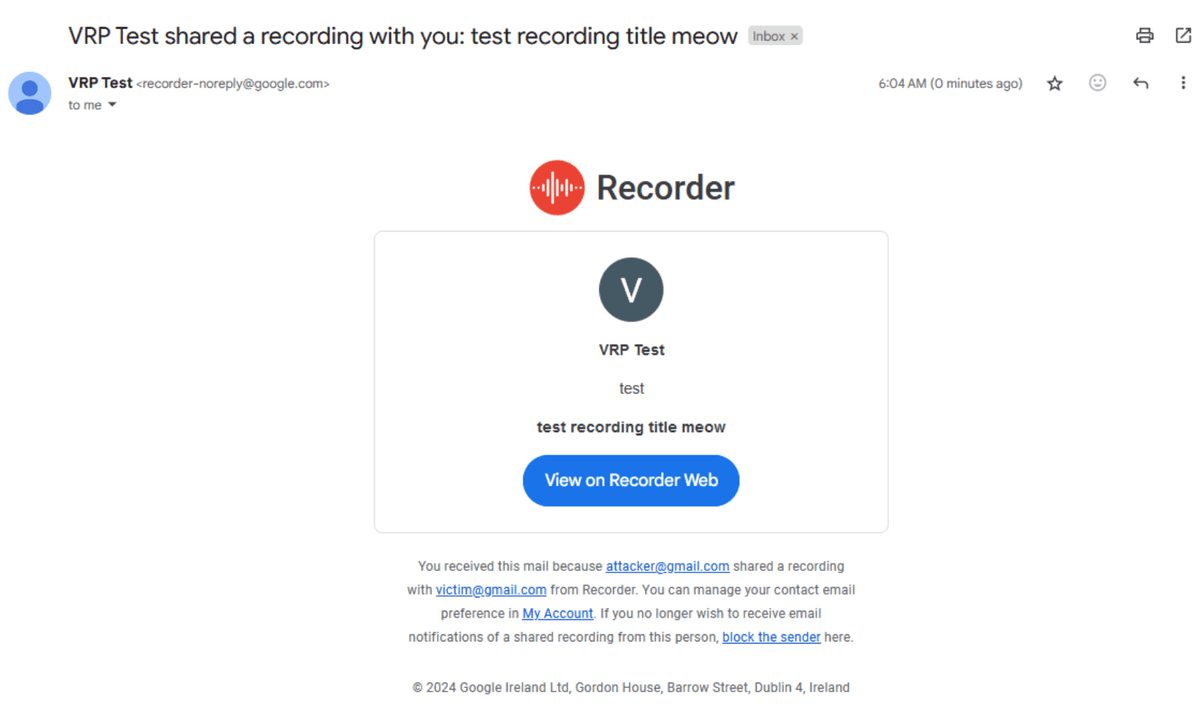
So, Skull noticed that the title of the recording would become the subject of the email, so he changed the title of the recording to 2.5 million characters.
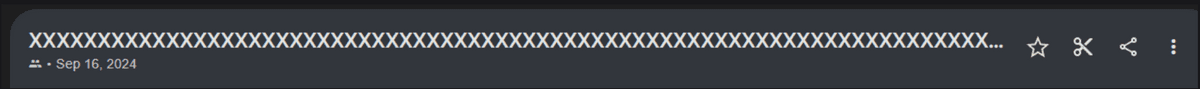
By making the title so long, the email was not sent, and the victim was able to obtain the email address of the Google account from the YouTube account without being noticed.
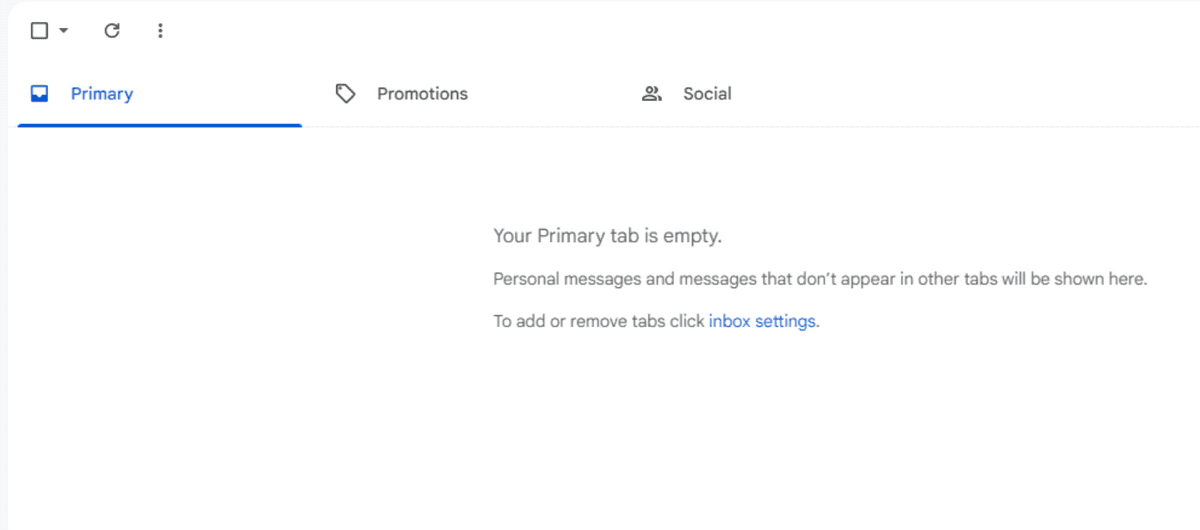
Skull reported the issue to Google on September 15, 2024, and Google applied a fix on February 9, 2025. Google said it was 'highly exploitable and has a large impact,' but that the 'attack chain is complex,' so it lowered the reward rank by one level and paid Skull a total of $10,633 (approximately 1.64 million yen).
Related Posts:
in Web Service, Security, Free Member, Posted by log1d_ts