A problem was discovered where phone numbers linked to Google accounts could be found by brute force
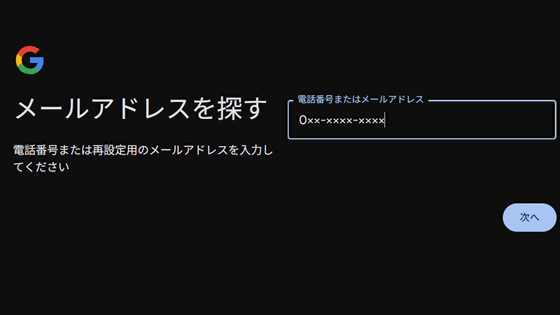
It is possible to link a phone number to a Google account, which can be
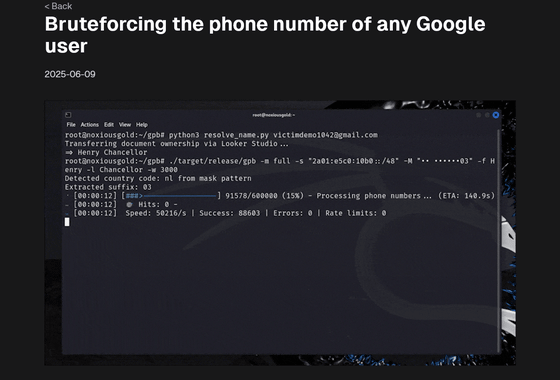
Bruteforcing the phone number of any Google user
https://brutecat.com/articles/leaking-google-phones
Google fixes bug that could reveal users' private phone numbers | TechCrunch
https://techcrunch.com/2025/06/09/google-fixes-bug-that-could-reveal-users-private-phone-numbers/
An independent researcher who publishes cybersecurity-related research on the blog 'brutecat' reported a vulnerability in Google's account recovery process in April 2025 when entering a phone number. According to brutecat, a traditional username recovery form that does not use JavaScript remained accessible, and the form was able to derive the correct number by using a script to brute-force every combination. Below is a demonstration video of the script actually identifying a phone number.
Leaking the phone number of any Google user ($5k bounty) - YouTube
In fact, brutecat is working with technology media TechCrunch to test how to identify phone numbers associated with accounts. First, TechCrunch created a new Google account with a random email address and set a phone number that had never been used for linking to the account. Then, they provided brutecat with only the registered email address. As a result, brutecat was able to correctly identify the phone number set by TechCrunch.
If your phone number is identified, not only will your private number be exposed, but there is also the risk of resetting the passwords of any accounts through SIM swap fraud . In addition, the phone number associated with your Google account can be used for the account recovery process, so even if you don't know the login password, you can use the phone number to access your account and take over it.

Because the state in which phone numbers can be identified by scripts is a critical vulnerability, brutecat and TechCrunch kept their findings secret after reporting it to Google through the Vulnerability Reward Program (VRP) . On June 6, 2025, Google reported to both media outlets that it had completely abolished the old account recovery process, and Google awarded brutecat, who reported the bug, $5,000 (about 720,000 yen) in bounty money and prizes.
'This issue has now been fixed. We would like to thank the researcher who reported this issue,' said Google spokesperson Kimberly Samra. 'We always emphasize the importance of collaborating with the security research community through our vulnerability bounty program, and reports from researchers like this one help us find and fix issues quickly to keep our users safe.'
Related Posts:
in Software, Web Service, Video, Posted by log1e_dh