A messaging app that touted itself as 'ultra-secure' has leaked everyone's phone numbers and PINs

A messaging app that was marketed as being extremely secure was found to have multiple vulnerabilities during security testing. The app was fixed and relaunched under a new name, but further security testing revealed new vulnerabilities, including the complete exposure of users' phone numbers.
'Super secure' MAGA-themed messaging app leaks everyone's phone number :: Eric Daigle
Converso is an instant messaging app that was launched in 2023, and its features include 'implementing cutting-edge end-to-end encryption,' 'not collecting metadata,' and 'using a distributed architecture that does not use any servers.'
However, after reverse engineering and traffic analysis, security researcher crnković found that all of the claimed features were unfounded.
For example, a copy of all encrypted messages was uploaded to a publicly accessible 'open Firebase bucket,' meaning anyone with an internet connection could read every message sent on the app.
The encryption function itself used an existing end-to-end encryption service called 'Seald,' but there was an implementation error that made it possible for anyone to guess the private key from public information. Furthermore, while the service advertised itself as decentralized, it actually used a standard centralized server and used a third-party provider to store messages.
Converso CEO Tanner Haas responded to the report by Crnković and others, threatening legal action and accusing the company of being a shill for rival app Signal. Converso was subsequently removed from the App Store and Google Play Store 'to address and improve its features.'
However, Converso was relaunched under the name ' Freedom Chat .' Apparently, Converso's user base was biased toward conservative Americans, and the rebranding clearly narrowed the app's target to conservatives. For example, the screenshot prevention feature is explained as being designed with consideration for 'conservatives' complicated circumstances regarding screenshots,' and conservative influencers are displayed as recommended users.
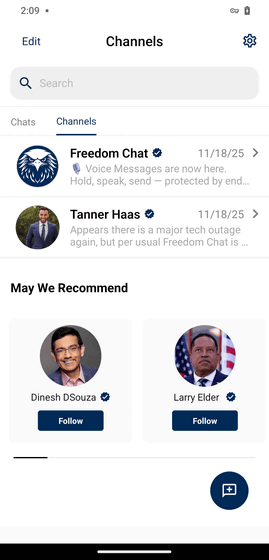
So, when security researcher Eric Daigle and others examined the security of Freedom Chat, they discovered two serious problems.
First, we discovered that when retrieving a list of participating members in Freedom Chat's channel function, information including each user's PIN (personal identification number) was sent. Unless a user left the Freedom Chat channel they were added to by default, all users' PINs were exposed to other users.
Freedom Chat also criticized the vulnerability of WhatsApp's contact discovery function, but Freedom Chat also had a similar API endpoint. This API returned the status of whether or not a user was using Freedom Chat and the user ID when a phone number from the contact list was sent, but there was no limit on the frequency of access.
Daigle then created a script to automatically generate valid seven-digit phone numbers in the United States and send them to the API in batches of 40,000. After adjusting the script to avoid excessive load on the server, Daigle was able to test all US phone numbers in just over 27 hours without any errors. This allowed him to identify the phone numbers of all Freedom Chat users. By matching the user IDs obtained with the PINs leaked from the channel information, it was possible to link the phone numbers to the PINs.
The vulnerability in Freedom Chat was discovered on November 23, 2025, and reported to Freedom Chat support on December 4. Freedom Chat responded the following day, explaining the PIN specifications and stating that they had already added audit procedures, and notified the company that the issue had been fixed on December 9.
Related Posts:
in Software, Smartphone, Security, Posted by log1i_yk