It turns out that a Chinese-made KVM is secretly equipped with a microphone, and there are also traces of communication with a Chinese-based server

It has been discovered that
How I discovered a hidden microphone on a Chinese NanoKVM
https://telefoncek.si/2025/02/2025-02-10-hidden-microphone-on-nanokvm/
Researcher finds Chinese KVM has undocumented microphone, communicates with China-based servers — Sipeed's nanoKVM switch has other severe security flaws and allows audio recording, claims researcher | Tom's Hardware
NanoKVM is a KVM switch developed by the Chinese company Sipeed. It's cheaper than competitors and allows users to remotely control computers and servers using a virtual keyboard, mouse, and monitor. It quickly gained attention online, but a Slovenian security researcher has discovered some serious flaws.
According to the researcher, the initial batch of this device had a default password that could be used to access SSH. This vulnerability was fixed after the researcher reported it to Sipeed. Although this issue was quickly addressed, NanoKVM had many other issues.

For example, there were flaws in the user interface. NanoKVM's user interface had many issues, including no
Another concern was the device's reliance on Chinese DNS servers, communication with Chinese Sipeed servers, and downloading updates as well as closed-source components, the keys for verifying these components being stored in plaintext on the device. Other concerns included a lack of integrity verification of software updates, the inclusion of a specialized version of the WireGuard VPN application that doesn't work on some networks, and the fact that it runs a heavily limited version of Linux, lacking systemd and apt .
Even more alarming was the presence of tcpdump and aircrack, tools commonly used for network packet analysis and wireless security testing. While useful for debugging and development, these tools are also potentially exploitable hacking tools and should not be present on production devices.
The best part was that it had a built-in microphone measuring just 2mm x 1mm, which is not specified in the official documentation. All the necessary recording tools were installed on the device by default and were easily accessible from outside via SSH.
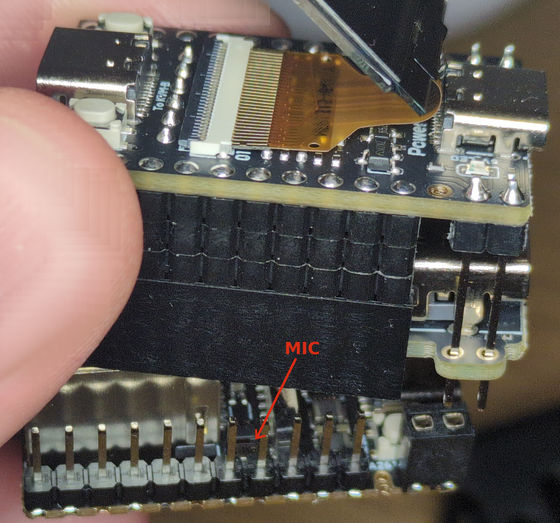
While it was possible to physically remove the microphone, disassembling the device was difficult, and because the microphone is so small, a microscope or magnifying glass was required to properly desolder it.
'In summary, this device is riddled with security flaws. We believe these issues stem from extreme carelessness and rapid development, not malicious intent on the part of the developers. However, this does not make it any less of a concern,' the researchers wrote.
Fortunately, because NanoKVM is nominally open source, community members have begun porting it to alternative Linux distributions, allowing users to use the version they prefer.
Related Posts: