Let's Encrypt announces that it will reduce the validity period of its certificates to 45 days

On December 3, 2025, local time,
Decreasing Certificate Lifetimes to 45 Days - Let's Encrypt
https://letsencrypt.org/2025/12/03/from-90-to-45
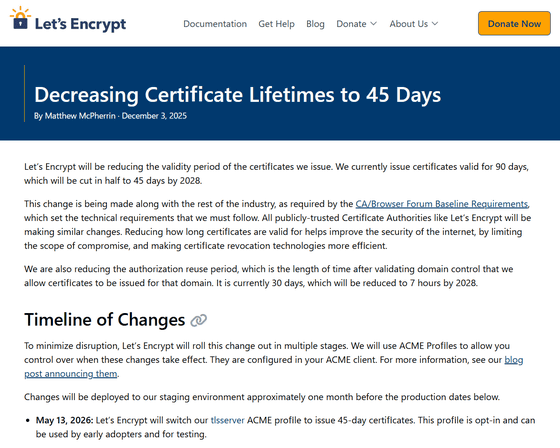
The CA/Browser Forum , an industry group of certificate authorities, internet browser vendors, and other application providers that use X.509 digital certificates for TLS and code signing, has established baseline requirements that define the technical requirements that Let's Encrypt must adhere to. Based on these baseline requirements, Let's Encrypt has announced that it will work with the industry to shorten certificate expiration dates to 45 days by 2028.
Let's Encrypt explains that shortening the certificate expiration period to 45 days will improve internet security by limiting the scope of breaches and promoting the efficiency of certificate revocation technology. They also plan to shorten the certificate reuse period, the period during which a certificate can be issued for a domain after domain control verification. This certificate reuse period is currently 30 days, but is expected to be reduced to seven hours by 2028.
To minimize disruption, Let's Encrypt will roll out the changes in stages, as detailed below.
May 13, 2026: Let's Encrypt will switch its ACME profile for TLS servers to issuing 45-day certificates. This profile is opt-in and available for early adopters and testing.
February 10, 2027: Let's Encrypt will switch the default Classic ACME profile to 64-day certificate issuance with a 10-day certificate reuse period. This will affect all users who have not opted in to the TSL server or short-lived (6-day) profile.
February 16, 2028: We will further update the Classic ACME profile, switching to 45-day certificate issuance with a 7-hour certificate reuse period.

Let's Encrypt explains that 'most users who automatically issue certificates will not need to change any action,' but encourages ACME clients to use
Also, because the certificates will have a shorter validity period, 'manual certificate renewal is not recommended,' Let's Encrypt wrote, and recommended making sure your systems have sufficient monitoring capabilities to provide appropriate alerts if certificates aren't renewed on schedule.
The most challenging aspect of automated certificate issuance is proving domain control. Reducing certificate validity periods and certificate reuse periods requires users to prove control more frequently. All validation methods in use at the time of writing require the ACME client to have real-time access to the user's infrastructure. As such, there has long been a need for a way to run ACME clients without granting them access to sensitive systems.
So Let's Encrypt is working with our partners at the CA/Browser Forum and IETF to standardize a new validation method called DNS-PERSIST-01 , which is great because it eliminates the need to change the DNS TXT entry used to prove control with every update.
This means that a single DNS entry can be configured and certificates can be automatically renewed without the need for a separate DNS update mechanism. This will enable more users to automate certificate renewals and reduce reliance on credential reuse, as DNS records will not be changed without ACME client intervention. DNS-PERSIST-01 is expected to be available in 2026.

On the social message board Hacker News , many people supported shortening the certificate expiration period , but also expressed anticipation for the arrival of DNS-PERSIST-01 and urged an end to certificate pinning .
Related Posts:
in Web Service, Posted by logu_ii