A vulnerability in the FIA's system that manages F1 driver information was exploited to access Max Verstappen's personal information

Hacking Formula 1: Accessing Max Verstappen's passport and PII through FIA bugs
https://ian.sh/fia

We became an admin in the Fédération Internationale de l'Automobile's driver categorization system, which allowed us to access the PII and password hashes of any rated driver, including Max Verstappen. 🏎️
https://t.co/vdX7OegqmW — Ian Carroll (@iangcarroll) October 22, 2025
Carroll is the founder of the flight search service seats.aero , and in addition to his work, he does security research on bug bounties, transportation, and other interesting areas.
ian carroll
https://ian.sh/
F1 drivers need an 'FIA Super License' to compete in races. FIA Super Licenses are issued annually by the motorsport authorities of the driver's home country, and in order to be issued, drivers must earn license points in races, and there are age restrictions and a document review.
F1 drivers are also classified into four driver categories: Bronze, Silver, Gold and Platinum. These are separate from the Super Licence system, but are managed through the FIA Portal, and holding an active Super Licence automatically grants Platinum status.
According to Carroll, it is possible to create an account in the driver's category system using an email address and password. To be categorized, you need to upload identification and driving experience, but Carroll discovered a very simple HTTP PUT request used to update the user profile.
While the request itself contained nothing interesting, the JSON returned in the response contained extraneous values, such as 'ID,' 'Email address,' 'Last name,' 'First name,' 'Keep name private,' 'Nickname,' 'Birthday,' 'Gender,' 'Token,' 'Role,' 'Country,' 'Filter,' 'Status,' and 'Secondary email address.'
The inclusion of 'roles' raised the possibility of a privilege escalation, so Carroll examined the JavaScript to see if there was any related logic. He discovered that there were roles intended for use by drivers, FIA staff, and site administrators. Naturally, he could infer that the most important role would be 'admin,' so he guessed the format of the PUT request and sent it as admin. It worked as expected, allowing Carroll to gain the site administrator role.
After re-authenticating and logging in to refresh the session, Carroll was taken to a completely different dashboard for site administrators. To verify his findings, he loaded the driver's profile and found personally identifiable information (PII) such as password hashes, email addresses, phone numbers, passports, and resumes.
Below is a screenshot shown by Carroll, which shows that Verstappen's information is available.
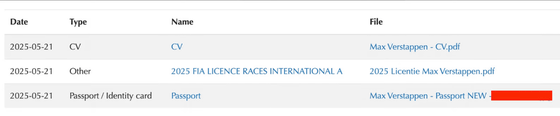
Carroll informed the FIA of the vulnerability via email and LinkedIn. The FIA immediately took the site offline and implemented a fix. Carroll said he did not obtain any personal information and destroyed all test data.
According to Carroll, this case is just one of the vulnerabilities the FIA had.
Related Posts:
in Posted by logc_nt