Microsoft warns of a cyber attack called Payroll Pirates, which allows users to transfer their payroll to unknown accounts

Microsoft has warned of an increasing number of cyberattacks known as ' payroll pirates, ' in which attackers take over employee accounts
Investigating targeted “payroll pirate” attacks affecting US universities | Microsoft Security Blog
https://www.microsoft.com/en-us/security/blog/2025/10/09/investigating-targeted-payroll-pirate-attacks-affecting-us-universities/
Microsoft warns of new “Payroll Pirate” scam stealing employees' direct deposits - Ars Technica
https://arstechnica.com/security/2025/10/payroll-pirate-phishing-scam-that-takes-over-workday-accounts-steals-paychecks/
According to Microsoft, the cyberattack, dubbed 'payroll pirates,' involves phishing emails that allow attackers to access victims' HR service accounts and steal their account credentials. Using man-in-the-middle tactics, attackers also steal victims' multi-factor authentication (MFA) codes.
Attackers use stolen credentials to log into HR services that manage employee personal information. They then change the bank account designated by the employee as the direct deposit of their salary to an account controlled by the attacker. This allows the attacker to pay the salary of the compromised employee. For example, in the case of Workday, when a bank account for direct deposit of a salary is changed, an email is sent to confirm this. To prevent this message from being sent, attackers create filters to block messages from Workday from appearing in the victim's email inbox.
'Threat actors targeted accounts at multiple universities to obtain credentials using realistic-looking phishing emails,' Microsoft reported. 'Since March 2025, we have confirmed that 11 accounts at three universities have been compromised and phishing emails have been sent to approximately 6,000 email accounts at 25 universities.'
The diagram below shows the entire process of a payroll piracy attack. The attacker (Storm-2657) contacts the victim with a phishing email. If the victim clicks on a URL in the email and enters their HR service account credentials on a fake website, the attacker steals the credentials. The attacker then uses these credentials to log in to the real HR service and change the payroll account to one controlled by the attacker, thereby stealing the victim's salary.
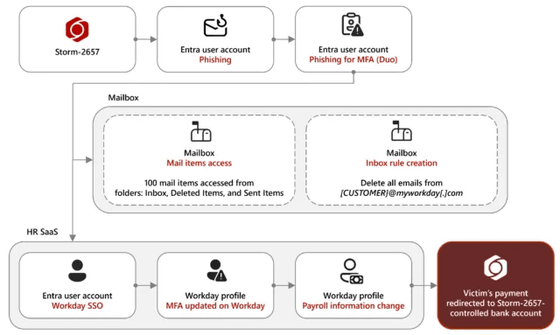
The phishing emails sent to victims claim that they may have been exposed to an infectious disease recently detected on their university campus or that there have been recent changes to their employee benefits. The emails contain URLs to pages where victims can confirm their exposure or view changes to their benefits. If victims visit these pages and enter their HR service account credentials, their information will be stolen.
In addition, by introducing FIDO-compliant MFA, such attacks can be prevented, so Ars Technica reported that 'highlighting the importance of introducing FIDO-compliant MFA.'
Microsoft recommends that you 'regularly check for email filtering rules that may block security-related emails from HR services such as Workday.'
Related Posts:
in Security, Posted by logu_ii







