The security feature 'Memory Integrity Enforcement' installed in the iPhone 17 and iPhone Air provides memory security that can defend against nation-state level hacking.
Apple
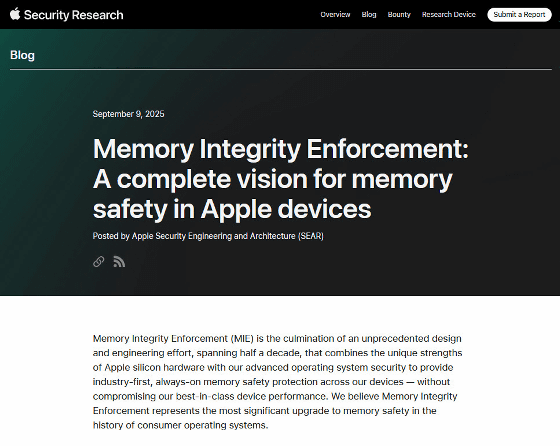
Blog - Memory Integrity Enforcement: A complete vision for memory safety in Apple devices - Apple Security Research
https://security.apple.com/blog/memory-integrity-enforcement/
According to Apple, there has never been a widespread malware attack on iPhones, and the only known attacks have been targeted by nation-state hackers. Targeted attacks often exploit memory safety vulnerabilities, and Apple has worked to improve memory safety to prevent these attacks.
For example, Swift , a programming language developed by Apple and used in many iOS and macOS apps, is designed with memory safety in mind, and iOS 15, released in 2021, introduced the kernel-level secure memory allocator kalloc_type . Furthermore, iOS 17, released in 2023, added the user-level memory allocator xzone malloc.
Enhanced memory safety extends beyond software to hardware. The A12 Bionic processor featured in the iPhone XS, iPhone XS Max, and iPhone XR, released in 2018, incorporates Pointer Authentication Code (PAC), which prevents exploitation of memory bugs. Furthermore, when Arm published its memory safety specification , the Memory Tagging Extension (PDF file) , in 2019, it thoroughly investigated and analyzed the issue, identifying vulnerabilities that Apple considered unacceptable. The Enhanced Memory Tagging Extension (EMTE) , incorporating fixes for these vulnerabilities, will be released in 2022.
As a culmination of these memory safety efforts, Apple has introduced Memory Integrity Enforcement (MIE) to the iPhone 17 series and iPhone Air. MIE is a comprehensive memory safety defense that spans both hardware and software, providing strong defense against various attacks while maintaining device performance.

The diagram below shows the timing (green) of the defense against various attacks. MIE can block many attack chains at a fundamental level, and it is impossible to 'reactivate the attack chain by inserting new bugs.'
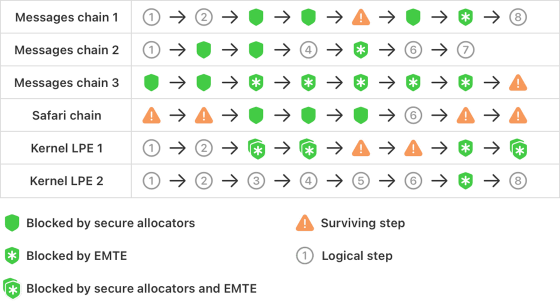
Apple has tested the effectiveness of MIE against 'highly sophisticated mercenary spyware attacks ' carried out over the past three years. 'MIE significantly increases the cost of developing and maintaining exploit chains. This will block the vast majority of the most effective exploit techniques of the past 25 years, and we believe it will fundamentally redefine memory safety in Apple products,' the company said. 'We believe MIE will be the most significant memory safety upgrade in the history of consumer operating systems.'
Related Posts:
in Hardware, Software, Smartphone, Security, Posted by log1o_hf