Iran's largest cryptocurrency exchange 'Nobitex' has over 13 billion yen stolen, the crime was committed by the pro-Israeli hacker group 'Gonjeshke Darande' and the aim was not financial but sanctions against terrorists.

On June 18, 2025 local time, Iran's largest cryptocurrency exchange, Nobitex, was subjected to a large-scale hacking attack. According to blockchain analysis company
Iranian crypto exchange Nobitex hacked for over $90 million by pro-Israel group
https://www.elliptic.co/blog/iranian-crypto-exchange-nobitex-hacked-pro-israel-group

Hackers steal and destroy millions from Iran's largest crypto exchange | TechCrunch
https://techcrunch.com/2025/06/18/hackers-steal-and-destroy-millions-from-irans-largest-crypto-exchange/
Iranian Exchange Nobitex: The $90M Exploit
https://www.chainalysis.com/blog/nobitex-iranian-exchange-exploit-june-2025/
Gonjeshke Darande (Predatory Sparrow) revealed that he had launched a hacking attack on Nobitex on June 18, 2025, via his official X account. The contents of Nobitex's statement of responsibility are as follows:
'Within 24 hours, we will be publishing Nobitex source code and internal information from our internal network. All remaining assets at that point will be at risk. Nobitex is at the center of the Iranian regime's efforts to raise terrorist funds around the world and is also the regime's favorite tool for violating sanctions. We, Gonjeshke Darande, have launched a cyberattack against Nobitex. Nobitex does not even pretend to comply with sanctions. Instead, it exposes its users to the ways in which their infrastructure can be used to circumvent sanctions. The regime's dependency on Nobitex is also evident from the fact that working at Nobitex is considered essential to the regime's operations and counts as valid military service. Our cyberattack is due to Nobitex being a key regime tool for terrorist financing and sanctions violations. Involving in the regime's terrorist financing and sanctions violation infrastructure puts your assets at risk. Take action before it's too late!'
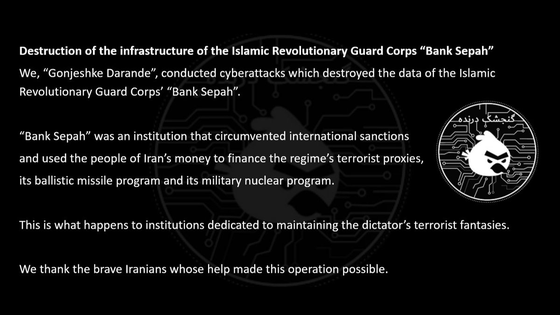
After the IRGC's “Bank Sepah” comes the turn of Nobitex
— Gonjeshke Darande (@GonjeshkeDarand) June 18, 2025
WARNING!
In 24 hours, we will release Nobitex's source code and internal information from their internal network.
Any assets that remain there after that point will be at risk!
The Nobitex exchange is at the heart of the… pic.twitter.com/GFyBCPCFIE
Elliptic points out that most of the cryptocurrency stolen from Nobitex was sent to cryptocurrency wallets using vanity addresses whose public keys contain words such as 'Fuck IRGC terrorists.' The IRGC is a military organization separate from the Iranian military and is designated as a terrorist organization and subject to sanctions in various regions, including the United States, Canada, the United Kingdom, and the EU.
Below is an example of a wallet to which cryptocurrency stolen from Nobitex could be sent.
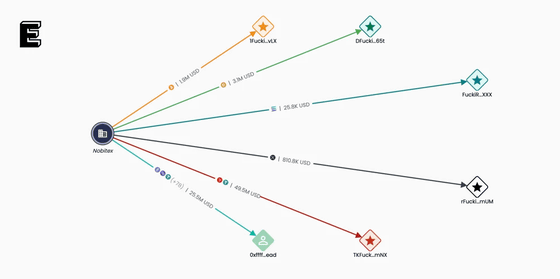
Elliptic points out that 'Gonjeshke Darande did not hack Nobitex for financial gain, so he does not hold the private keys to the wallets to which the stolen cryptocurrencies are sent.' Therefore, Elliptic describes the funds stolen from Nobitex as effectively 'burned.' In addition, Elliptic co-founder Tom Robinson
Nobitex, Iran's leading cryptocurrency exchange with over 7 million users, has been linked to the IRGC and Iranian government officials in the past. Investigations to date have revealed that relatives of Iran's Supreme Leader Ayatollah Ali Khamenei and business partners with ties to the IRGC are connected to Nobitex.
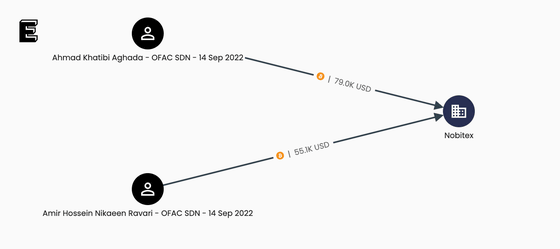
Elliptic has also identified Nobitex as being used in the past by sanctioned IRGC operatives who were sanctioned by the U.S. Office of Foreign Assets Control (OFAC) in September 2022 for 'distribution of ransomware BitLocker' and 'linked to Afkar System Yazd Company, which facilitates cyber threats.'
The IRGC answers only to the Iranian Supreme Leader, not the president, and exerts significant control over many sectors of the country's economy, including oil trading, which has allowed it to evade sanctions and fund Iranian-affiliated groups operating in other regions.
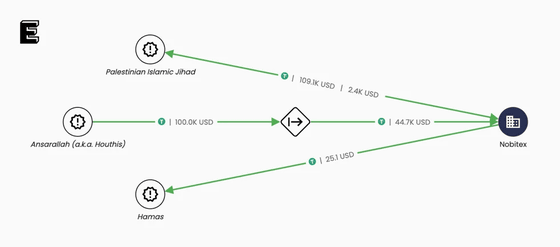
Nobitex, which is suspected to have ties to the IRGC, has been identified as funding cryptocurrency wallets linked to anti-government armed groups such as
Gonjeshke Darande is a pro-Israeli hacking group that claimed responsibility for a hacking attack targeting Iran's state-owned bank, Sepah Bank, on June 17, 2025. Gonjeshke Darande accused Sepah Bank of supporting the Iranian government's military finances, and the claim came after Israeli attacks on several Iranian military and other facilities .
Pro-Israeli hacktivist group 'Predatory Sparrow' claims responsibility for cyber attack on Iranian state-run Sepah Bank - GIGAZINE
Reuters is investigating the Sepa Bank hack, but was unable to immediately confirm whether it had been involved in the attack. However, the bank's website appears to have been taken offline on June 17.
At the same time, Israeli media reported that Sepah Bank customers were unable to access their accounts.
Gonjeshke Darande has been widely reported in Israeli media as a hacking group with ties to Israel, but Gonjeshke Darande has never officially acknowledged being sponsored by Israel.
Related Posts:
in Security, Posted by logu_ii






