It is clear that combining existing spyware with carefully planned phishing and social engineering can even bring about the collapse of a government

In December 2024, President Bashar al-Assad, who had ruled Syria for many years as a dictator, was attacked by the opposition and fled the country, leading to
How a Spyware App Compromised Assad's Army - New Lines Magazine
https://newlinesmag.com/reportage/how-a-spyware-app-compromised-assads-army/
Analysis of Spyware That Helped to Compromise a Syrian Army from Within
https://www.mobile-hacker.com/2025/06/05/analysis-of-spyware-that-helped-to-compromise-a-syrian-army-from-within/
An investigation into the technical aspects of the Assad regime's downfall has revealed that a spyware called 'STFD-686' was prevalent among Syrian military officers. According to security blog Mobile Hacker , the spyware stole sensitive data from smartphones and played a role in the downfall of the Syrian regime.
Regarding STFD-686, Mobile Hacker pointed out that 'spying on smartphones does not necessarily require expensive zero-day exploits or the development of sophisticated custom-made undetectable spyware. Rather, it shows that old, commercially available spyware can be combined with well-crafted phishing campaigns and social engineering to deliver lethal espionage.'

Weakened by a decade of war and a severe economic collapse, the Syrian army had seen its soldiers' salaries plummet to just $20 a month, creating an environment in which it was easy to exploit Syrian officers and soldiers.
In the early summer of 2024, a smartphone app called STFD-686 (Syria Trust for Development) began circulating among Syrian military officers. The app was distributed through a Telegram channel also named 'Syria Trust for Development,' a humanitarian aid organization overseen by
The Syrian soldiers used STFD-686 because the app promised to send them about $40 in cash every month. After installing the app, users had to fill out a survey, which allowed attackers to collect data from the soldiers.
The survey screen that appears when the app is launched is shown below. Mobile Hacker points out that this is a type of phishing .
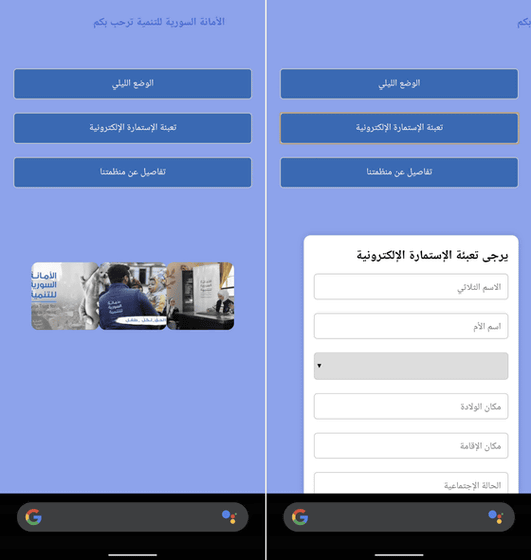
By answering this questionnaire, attackers could collect military information such as the user's phone number, military rank, division, and location, giving the rebels access to data that could be fed into military algorithms to create accurate battlefield maps, Mobile Hacker said.
STFD-686 uses a remote access trojan called 'SpyMax' that targets Android. SpyMax is part of a malware family called SpyNote, which was first spotted in darknet forums around 2018. SpyMax is designed to stealthily infiltrate Android devices, giving attackers complete control over the infected smartphone, including the ability to monitor the camera and microphone, track the phone using GPS, and intercept messages.
Initially, SpyMax was sold and sold on hacking forums, but eventually it became freely accessible to a wider range of cybercriminals, who began using it for targeted surveillance and crimeware attacks.
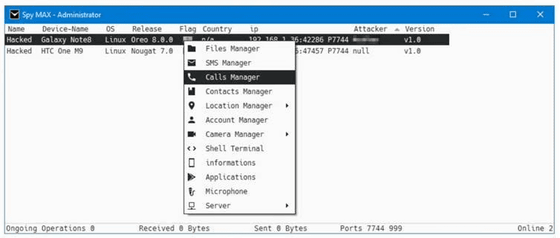
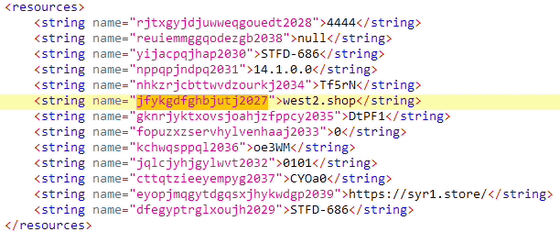
STFD-686 was distributed on a Telegram channel and used two domains for communication: a phishing domain (syr1.store) to lure user data, and a C&C server (west2.shop) to download the payload and exfiltrate data.
When Mobile Hacker analyzed these domains, they found several similar apps using the same domains. These similar apps are:
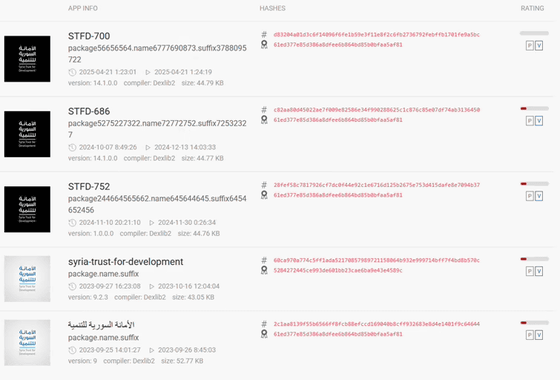
There were also cases where the same C&C server was used, but a different phishing site (syr1.online) was used.

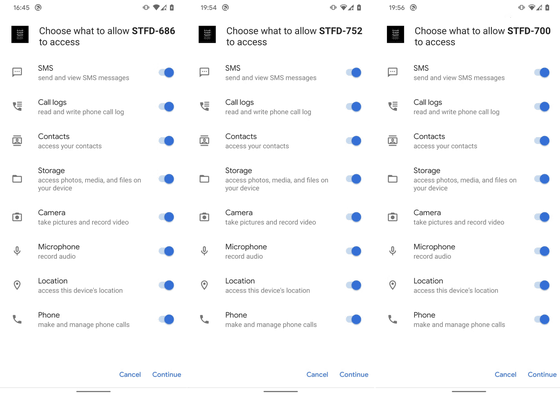
When these apps are installed on a smartphone, they pretend to be normal and request access to contacts, messages, camera, microphone, location, etc. Below are screenshots of the permissions requested by STFD-686 and similar apps.
The domains that the spyware communicates with are hardcoded in the APK resources.
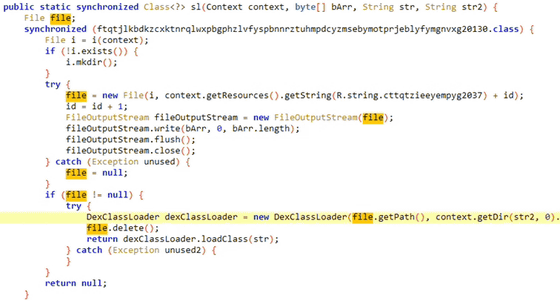
The main difference between SpyMax and other commercial spyware is that SpyMax does not have all the malicious functionality implemented in the main app (in this case the app downloaded from the Telegram channel) - it is designed to communicate with a C&C server and download each functionality as an APK or payload as needed.
While Mobile Hacker claims they were unable to obtain the actual payload, SpyMax uses eight payloads by default, which allow SpyMax to stream the camera from the device, record audio using the microphone, track the device's location, keylog user input, upload and download files from the mobile device, and steal SMS, contacts, and call history from installed apps.
The rebels' primary reason for using SpyMax was to obtain dynamic intelligence on the Syrian Army's operational status. The collected personal information, combined with real-time monitoring capabilities, allowed the attackers to identify officers in sensitive positions such as battalion commanders and communications officers, create live maps of force deployments that charted both strongholds and gaps in the Syrian Army's defenses, assess the actual size and strength of deployed forces, and access phone conversations, text messages, classified documents, and maps.
Mobile Hacker noted, 'What makes this attack unique is that, unlike other spyware campaigns that typically target individuals, it appears to have focused on compromising entire military institutions through primitive but destructive phishing attacks using Android spyware.' This case shows that espionage does not require expensive zero-day vulnerability exploits or sophisticated spyware, and that a combination of commercial tools like SpyMax with clever phishing and social engineering 'can be very successful,' Mobile Hacker wrote.
Related Posts: