How secure are the credit card payment terminals in stores?

Swiss developer Stephane Glore explained how he disassembled and reverse engineered a credit card payment terminal commonly found in Switzerland.
Root Shell on Credit Card Terminal
What Glore found was a payment terminal called 'Yomani XR,' a common and ubiquitous model in Switzerland.

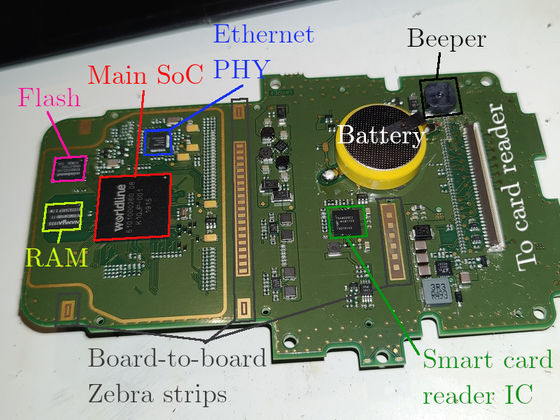
First, disassembly. It's made up of multiple PCBs, a small connector board for the outward-facing connectors, the main board, and a vertical board that holds the card slots. The main SoC appears to be a custom ASIC, a dual-core Arm processor codenamed 'Samoa II' in the firmware. Next to the SoC is a small external flash and RAM.
This type of device usually has a tamper detection switch, but this terminal does not have one in the form of a switch, and instead seems to detect tampering by contact with the flexible cable. With this method, even loosening even a part of the screw will break the contact and be considered tampering.
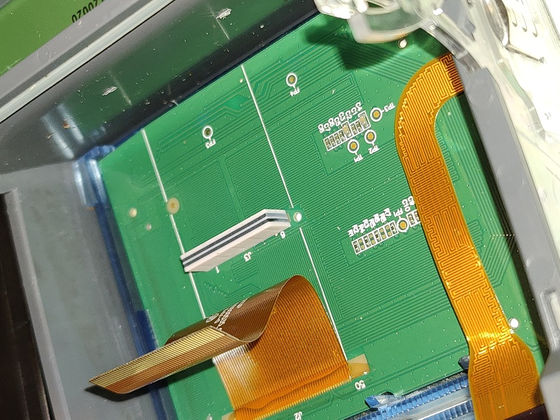
In fact, when Mr. Gloa reassembled it, a tamper detection warning was displayed.
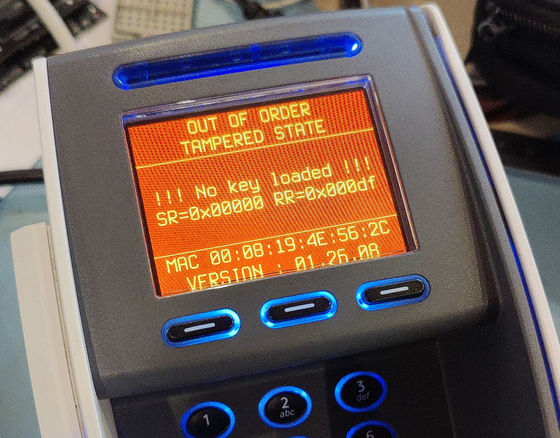
Next, Glore decided to read the contents of the chip.
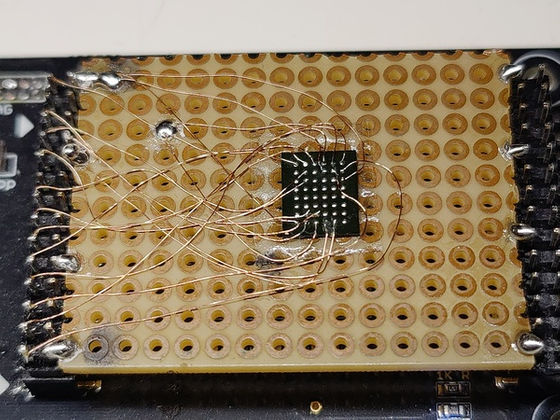
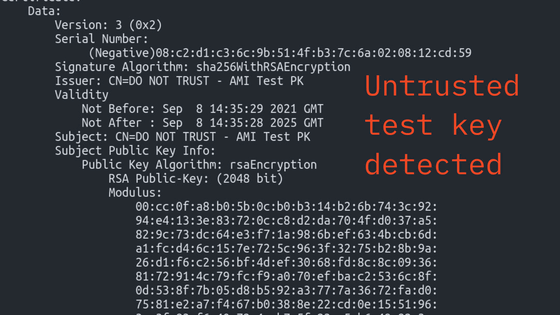
Looking at the contents, the researchers found that an unusual error-correcting code layout was implemented, that the device was running Linux, that the system was running the 3.6 kernel, that it was built with Buildroot 2010.02 in February 2023, and that it appeared to be using a custom bootloader called 'Booter v1.7.'
Now that he knew Linux was running, Glore was sure he had a console for debugging, so he used a logic analyzer to examine each circuit. He found the Linux boot log and was able to read the login prompt. Out of curiosity, he typed in 'root' and was able to log in.
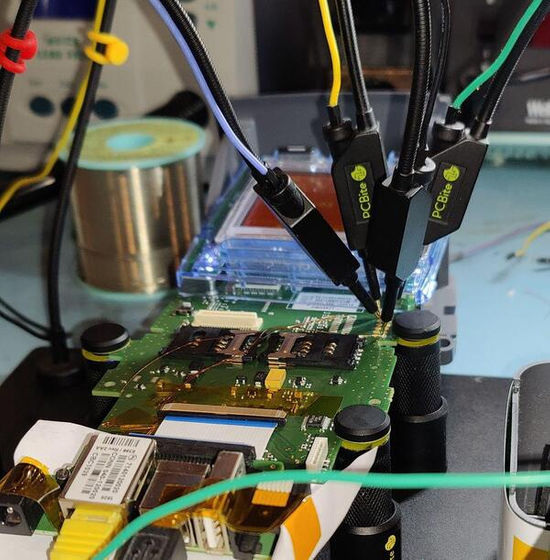
'You don't need sophisticated exploit chains or brute force attacks to see what's inside,' Glore points out. 'The serial port needed to peek is accessible from the outside. A small hatch on the back of the device gives you access to the debug connector without having to open the device and activate the tamper protection. All an attacker needs is 30 seconds to connect to the serial port, log in, deploy their malware, and walk away.'
However, the secure image that handles card numbers and keypads is properly encrypted and signed, so even if someone looked inside it, they would not be able to extract any personal information.
Glore concluded, 'It doesn't appear to be as big a risk as we initially feared, but it remains an unnecessary hole. I believe it was a significant oversight on the part of the engineers, but I have found no evidence that sensitive data such as card details could be leaked in this way. My guess is that a debug function accidentally made it into the production firmware at some point. It's likely that the issue was discovered and fixed in-house before I reported it to the manufacturer.'
Related Posts: