College students discover dating app that leaks privacy

Alex Shapiro, a 26-year-old computer science student at Yale University, reported that he had discovered a major security risk in a new dating app called 'Cerca.'
Yale student exposes data leak in college dating app - Yale Daily News
How Broken OTPs and Open Endpoints Turned a Dating App Into a Stalker's Playground | Alex Schapiro
https://alexschapiro.com/blog/security/vulnerability/2025/04/21/startups-need-to-take-security-seriously
Shapiro started working on this issue after a friend of his received a suspicious text message on Cerca that suggested he had a secret admirer. Because dating apps require a lot of personal information, Shapiro decided to check the safety of Cerca before his friend started using it.
First, Shapiro tested Cerca using a publicly available proxy app for iOS and found that it could read one-time passwords (OTPs), meaning that anyone with a phone number could access the account.
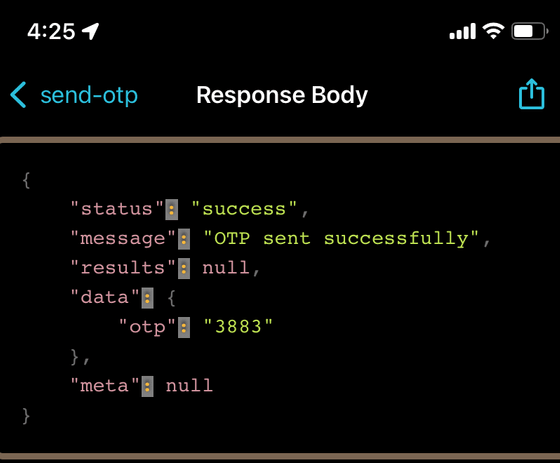
Furthermore, when they analyzed the communications using tools used in security and penetration testing, they found that a development endpoint that listed all the functions the app could perform was exposed, and when they accessed an endpoint named 'Users' from there, they found all the information about each account in the database.
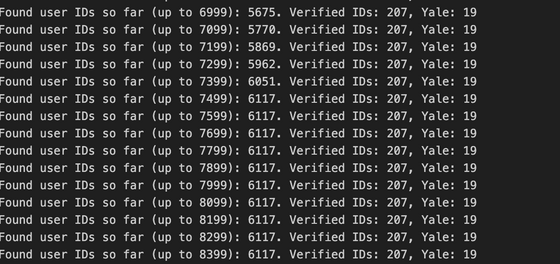
Shapiro wrote a simple Python script to identify valid IDs, but was able to sift through the database, extracting basic information like name, gender, and age, as well as highly sensitive information like passport and driver's license scans and sexual orientation.
For example, of the 6,117 users the script identified, 19 were Yale students. To avoid violating privacy, Shapiro did not look at the specific data, but it's entirely possible that a malicious actor could have exploited this vulnerability.
Cerca, a dating app launched by students at Georgetown and USC and rolled out to multiple universities, including Yale, requires users to have at least one potential match in common with them, which is why it touts the service as safe, even though Shapiro's findings suggest otherwise.
So, on February 24, 2025, the day after he noticed the problem, Mr. Shapiro contacted Cerca to inform them. The Cerca representative understood the seriousness of the problem, thanked Mr. Shapiro, and promised to address the problem promptly and notify affected users.
However, despite Shapiro checking in twice since then to see if there was any progress on the response, Cerca had not responded, and there was no indication that affected users had been contacted about the incident.
So after Shapiro verified that the vulnerability had been fixed, he decided to disclose the issue on April 21.

'We were alerted to potential security concerns by a self-described researcher and took immediate action, including deploying same-day fixes and engaging an outside cybersecurity firm to audit and harden our platform. We have no evidence to suggest that any other unauthorized third parties have accessed user data since our founding,' Cerca told The Yale Daily News, an independent campus newspaper run by Yale students.
However, in Connecticut, where Yale University is located, data breaches are required to be reported within 60 days to both the state's attorney general and to consumers, and Cerca's failure to notify users of the security issue reported by Shapiro may be in violation of state law.
'When the data in question includes things like passport scans, sexual orientation or private messages, this isn't just a matter of feelings; it poses serious risks to a person's personal safety,' said Sean O'Brien, a cybersecurity researcher at Yale Law School.
'If malicious actors had exploited this issue, it could have led to all sorts of things, including identity theft, stalking, and blackmail,' Shapiro said. 'These types of vulnerabilities are really scary and have the potential to ruin your life overnight, so we urge users to put security first and not jump on the bandwagon of trending apps.'
Related Posts:
in Web Service, Security, Posted by log1l_ks







