TeleMessage, a modified version of Signal and WhatsApp used by US government officials, was hacked, leaking chats and contacts

In May 2025, it was discovered that US government officials were using a modified version of the app '
The Signal Clone the Trump Admin Uses Was Hacked
https://www.404media.co/the-signal-clone-the-trump-admin-uses-was-hacked/
TeleMessage, a modified Signal clone used by US government officials, has been hacked | TechCrunch
https://techcrunch.com/2025/05/05/telemessage-a-modified-signal-clone-used-by-us-government-officials-has-been-hacked/
Tech site 404 Media says Signal-like app used by Trump adviser was hacked | Reuters
https://www.reuters.com/business/media-telecom/tech-site-404-media-says-signal-like-app-used-by-trump-adviser-was-hacked-2025-05-05/
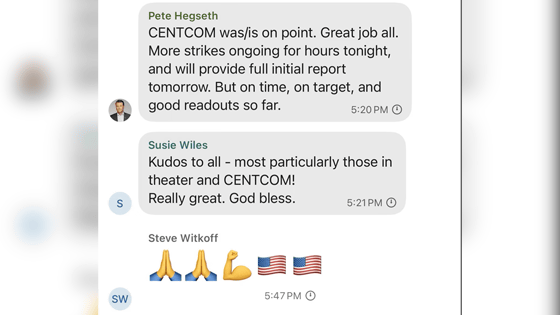
In March 2025, Michael Waltz , former National Security Advisor to the Trump Administration, accidentally added the editor-in-chief of monthly magazine The Atlantic to a Signal group chat, leaking top-secret military operations to the public .
At the time, it was noted that government officials were using Signal to communicate with each other, but it was later reported that Waltz was not using the official version of Signal, but a modified version of Signal called TeleMessage.
Trump administration official who accidentally leaked military secrets used an unofficial app to archive Signal messages - GIGAZINE

TeleMessage is an app that archives chats from encrypted messaging apps such as Signal, Telegram, and WhatsApp, and can archive not only text but also images and audio files. Archives are uploaded to a mail archiving vendor of your choice, but the end-to-end encryption implemented in Signal and other messaging apps does not work when archiving, which has been pointed out as a security risk.
404 Media recently reported that hackers hacked TeleMessage and stole data from customers who used modified versions of Signal, WhatsApp, Telegram, and other apps. 404 Media has not revealed the identity of the hackers, but says it is in contact with them. The messages and screenshots of the backend system reviewed by 404 Media reportedly contained data related to the U.S. Customs and Border Protection (CBP) , cryptocurrency giant Coinbase , and other financial institutions.
The hacker shared a screenshot of the TeleMessage backend panel with 404 Media below, which includes the user's name, phone number, and email address, and the email address ends with '@cbp.dhs.gov,' suggesting that the user is a CBP employee or related party.
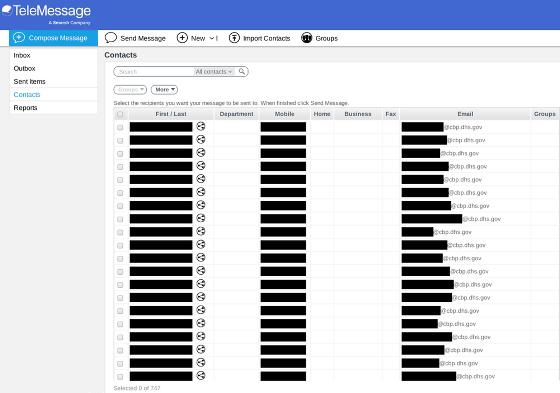
In fact, when 404 Media called some of the phone numbers believed to belong to CBP officials, the caller indeed identified himself as a person listed in the screenshot and confirmed that he was a CBP official. The voicemails obtained by the hackers also contained the name of a person believed to be a CBP official. In addition, messages believed to be from the cryptocurrency company Galaxy Digital included exchanges about a cryptocurrency bill being debated in the US Congress.
The hackers reportedly accessed a server hosted by AWS (Amazon Web Services) in northern Virginia, U.S., which TeleMessage uses. The hackers only accessed some of the data captured by the app, and the data they obtained did not include communications between senior U.S. government officials, but it is reported that they could have accessed much more data if they had wanted to.
The hacker told 404 Media that he targeted TeleMessage because he was curious to see how secure it was: 'The whole process probably took about 15-20 minutes. It wasn't hard at all,' he said, arguing that if he was able to hack it so easily, so could anyone else.
404 Media has not explained how the hackers hacked TeleMessage, citing the risk that others could exploit the vulnerability.
In response to an inquiry by tech media TechCrunch about the matter, TeleMessage's parent company Smarsh issued a statement saying, 'Upon learning of the potential security incident, we acted swiftly and engaged an external cybersecurity firm to investigate. As a precaution, we have temporarily suspended all TeleMessage services.'
Related Posts:
in Mobile, Software, Web Service, Security, Posted by log1h_ik